How to Lock or Unlock Your Domain: A Guide to What a Domain Lock Is and What it Does
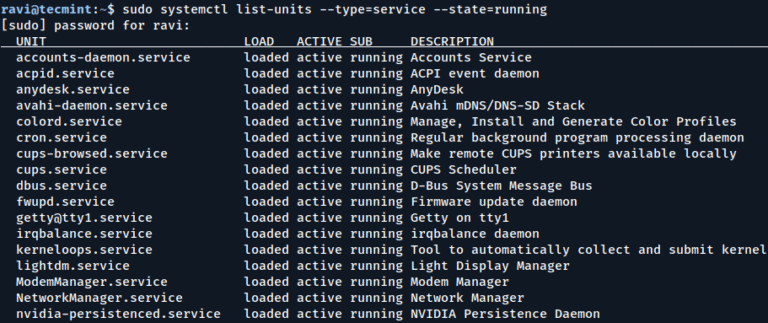
Welcome to our guide on locking and unlocking your domain name. Your domain name is your business’ virtual address. If you’re creating a website for your business, it’s important to understand how to secure your…