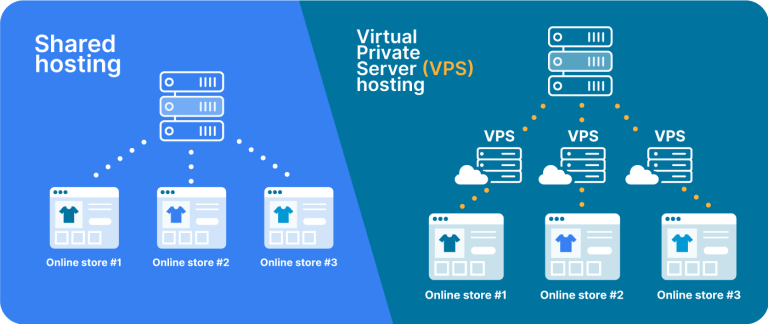
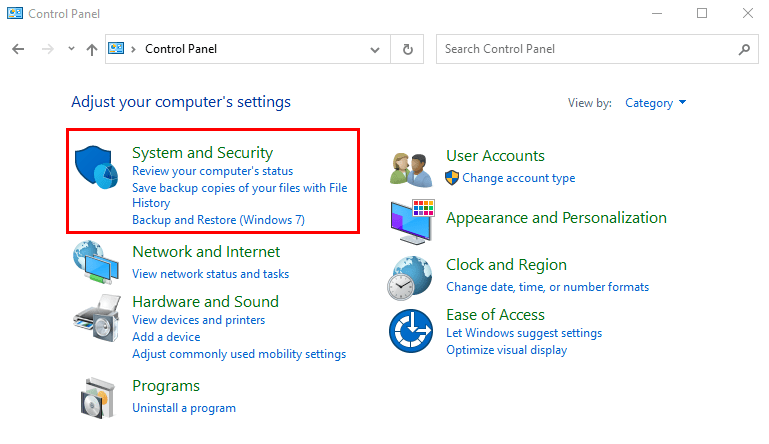
Your Complete .htaccess Guide: Including .htaccess Basics and More
Thanks for the tutorial. I’m trying to fix web site managed by others that somehow lost its .htaccess file. I know what the file does, but I’ve never had to re-create it once the site’s…