Want to protect your VPS from hackers? You’re not alone. Hacking is detrimental to any online presence, and organizations of all sizes are vulnerable to it if they don’t implement the proper security measures.
When it comes to your VPS, cyber threats can come in the form of malware, brute-force attacks, broken authentication, and more. Unless you configure your VPS properly and implement effective and efficient security measures, you may be putting your business at risk of security breaches.
This article will cover what you need to know about the risks of VPS hacking and provide a step-by-step guide to secure your VPS. It’ll also discuss the importance of choosing a reliable hosting provider and explore best practices for VPS management.
Let’s dive in.
Introduction to VPS Hosting and Security
Virtual Private Server (VPS) hosting is a type of web hosting that employs virtualization technology to create multiple virtual servers within a single physical server. Each virtual server operates independently, allowing users to have dedicated resources and complete control over their hosting environment. This makes it more cost-effective than dedicated hosting while offering more control and customization than shared hosting.
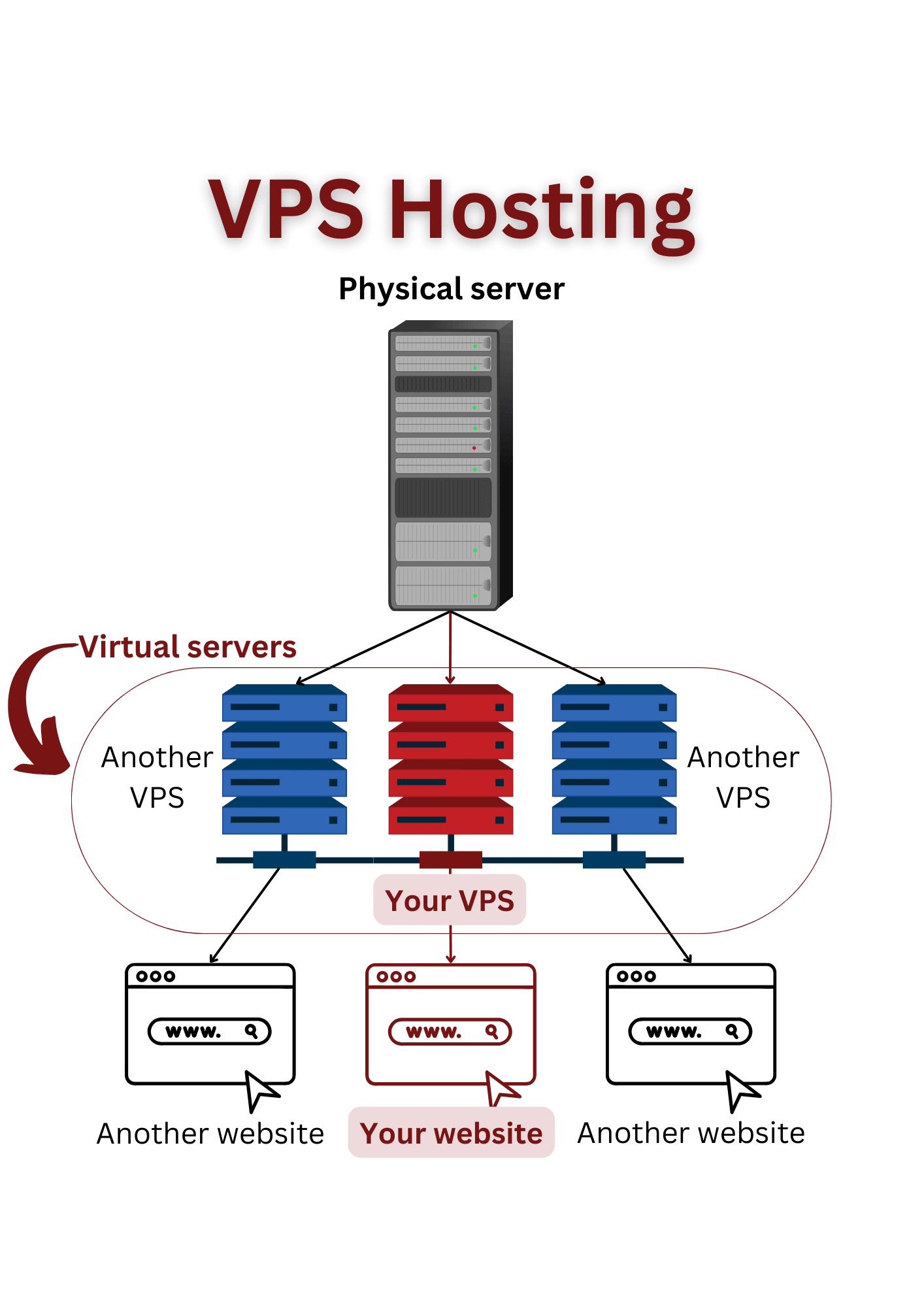
The VPS market is expected to grow by 14.53% over the next 5 years. However, just like any other hosting solution, a VPS is not immune to cyberattacks. In fact, due to the nature of shared resources, it can be vulnerable to cyber threats if not properly secured.
Why Configuring Your VPS Matters
Simply acquiring a VPS isn’t enough to guarantee a secure and stable hosting environment. Proper configuration plays a pivotal role in ensuring the integrity and performance of your online presence, safeguarding it from any malicious dangers.
Here are some of the benefits that you can harness by fine-tuning your Linux web server settings:
- Enhanced security – Implementing robust security measures such as firewalls, intrusion detection systems, and secure access protocols fortifies your hosting environment against unauthorized access and potential breaches.
- Optimal performance – Fine-tuning various parameters like resource allocation, network settings, and caching mechanisms ensures the seamless operation of your server.
- Scalability – Configuring your VPS allows for efficient scaling by allocating resources dynamically and handling traffic spikes effectively, ensuring your hosting environment can accommodate growing demands.
- Control and flexibility – Customizing software packages, frameworks, and libraries tailored to your needs provides greater control over your hosting environment, along with the ability to install monitoring and logging tools for proactive troubleshooting and maintenance.
That being said, you need to take proactive steps to secure your virtual hosting environment.
A Step-By-Step Guide to Secure Your VPS
Securing your VPS goes beyond the initial setup and requires careful consideration of security measures. With that in mind, we’ve carefully put together this step-by-step guide to help you secure your environment effectively and fortify your server, minimizing the risk of unauthorized access or data breaches.
Step 1: Access Your VPS Via SSH and Enable Public Key Authentication
Secure Shell (SSH) is a robust cryptographic network protocol that will allow you to securely connect to a remote machine or server over an unsecured network, like the internet, and perform various operations, including remote command execution, file transfers, and even tunneling other protocols.
Before granting access to a remote system, SSH verifies the identity of the user or client connecting to it using public-key cryptography, where the client presents a public key, and the server verifies it against a stored private key. This public key authentication process adds an extra layer of security, ensuring that only authorized users can access the remote resources.
Here is what you need to do to access your server using SSH with public key authentication:
For Windows Users
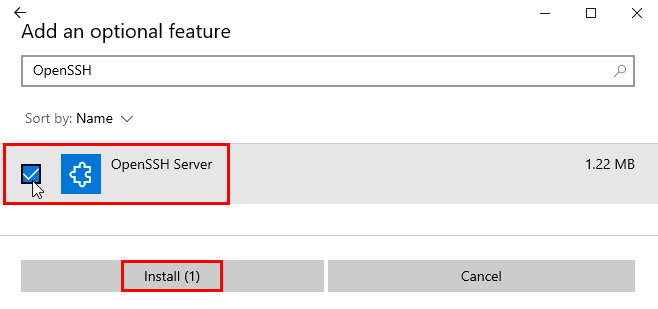
1. Make sure you have Git installed, then open the Command Prompt or PowerShell.
2. Type the following command to generate a new SSH key pair:
ssh-keygen -t rsa -b 4096You can choose a different type and bit size if desired.
3. Press Enter and provide a location to save the key pair when prompted. You can also leave it blank to use the default location.
4. Enter a passphrase. It is recommended to use a strong passphrase for added security. Note that the characters won’t be visible as you type.
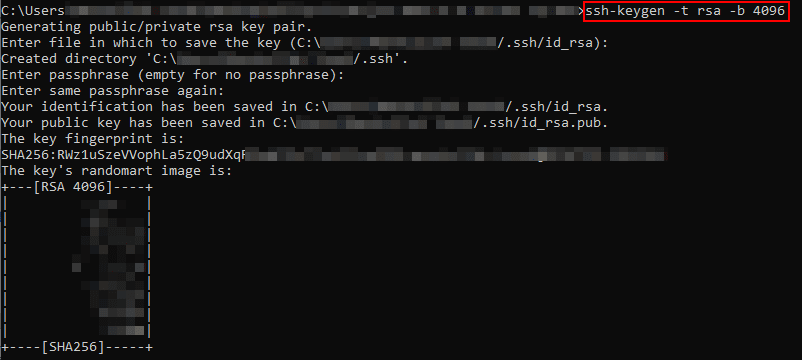
Then, the SSH key pair will be generated and saved to the specified location. The public key will have a .pub extension.
5. Make sure you have the IP address of your VPS, which is typically provided by your hosting provider, then type the following command, replacing username with your VPS username and your_vps_ip with the IP address of your VPS:
ssh username@your_vps_ipAlternatively, if you want to connect to your VPS using an application instead of the Command Prompt, you can follow these instructions after generating your SSH key authentication using the above steps:
1. Download and install PuTTY
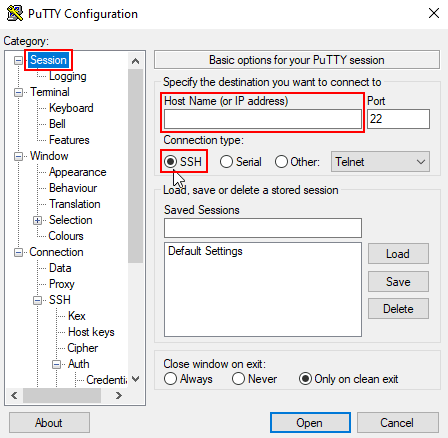
2. Launch PuTTY, go to the Session category, enter your VPS IP address in the Host Name (or IP address) field, and select the SSH option in the Connection type field.
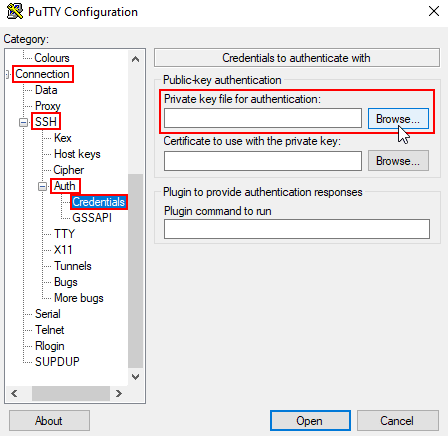
3. Go to the Connection category, expand the SSH menu, and select Auth. In the Private key file for authentication field, click the Browse button to locate and load your SSH private key file, then click Open to initiate the SSH connection.
You will now be connected to your server.
For Linux or macOS Users
1. Open the terminal application. You don’t need to install SSH since it’s readily available.
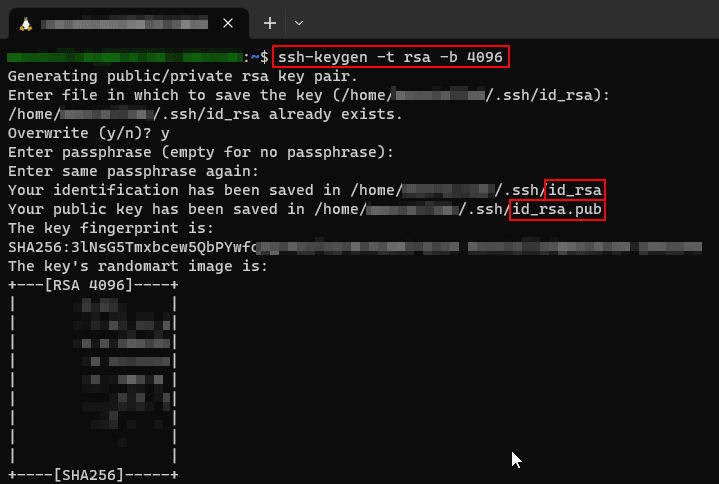
2. Execute the following command to generate a new SSH key pair:
ssh-keygen -t rsa -b 4096Change the bit size to your needs.
3. Press Enter and provide a location to save the key pair when prompted. You can leave it blank to use the default location.
4. You’ll be asked to enter a passphrase. Similar to Windows, it is recommended to use a strong passphrase for enhanced security.
5. Make sure you have the IP address of your VPS, which is typically provided by your hosting provider, then type the following command, replacing username with your VPS username and your_vps_ip with the IP address of your VPS:
ssh username@your_vps_ipYou might need to specify your private key using the -i flag:
ssh -i /path/to/private_key username@your_vps_ipYou’ll now be successfully connected to your server.
Step 2: Update Your Server and Software
Once you have connected successfully to your VPS, it’s essential to update your package manager to ensure access to the latest software packages and security updates. Depending on the Linux distribution you are using, the commands may differ slightly.
It is recommended to migrate to a VPS server running a current Linux OS distro that is not going end-of-life (EOL), such as AlmaLinux 8, Rocky Linux 8, or Ubuntu 22.04 LTS, to ensure that you still get security patches and bug fixes.
For Ubuntu (Debian-based) Systems
1. Run the following commands to fetch the latest package lists and upgrade any outdated packages on your system:
sudo apt update
sudo apt upgrade2. Install any required software packages for your specific needs. Use this command, replacing package_name with the name of the software you want to install:
sudo apt install package_name3. Upgrade the entire distribution to a newer release by running the following command:
sudo apt dist-upgrade4. After completing the updates, reboot your server.
sudo reboot5. Verify the updates by logging back into your server and running this command:
sudo apt list --upgradableFor CentOS (RHEL-based) Systems
We’ll do the same for CentOS, but by executing slightly different commands:
1. Fetch the latest package lists using this command and upgrade any outdated packages on your system:
sudo yum updatesudo yum upgrade2. Install any required software packages for your specific needs. Use this command, replacing package_name with the name of the software you want to install:
sudo yum install package_name3. For versions after CentOS 8 to CentOS Stream:
sudo yum install centos-release-stream
sudo yum distro-sync4. After completing the updates, reboot your server.
sudo reboot5. Verify the updates by logging back into your server and running this command:
sudo yum list updatesYou might also want to consider upgrading your server, depending on the traffic you experience and your specific goals.
Step 3: Create and Manage User Accounts
One of the key tasks that you should do to keep your VPS secure is creating and managing user accounts. User accounts will enable you to allow the individuals that you want to access your server to perform specific tasks without permitting them to take full control of your server. This will keep your VPS structured, organized, and safe from security risks.
You can assign user roles from a variety of user account types, each serving different duties and purposes.
| User Account Type | Description | Roles and Permissions |
|---|---|---|
| Root (Superuser/Administrator) | The root user has unrestricted access to the entire system. | Performs administrative tasks, system configuration, software installation, and user management. |
| Regular | Assigned to individuals needing access to the server for specific tasks or services. | Has limited permissions, can only access specific files and directories, and can’t perform administrative tasks. |
| Group | Assigned to a group of users with shared access and permissions. | Allows collaboration and shared access to files, directories, or resources. Specific permissions get assigned to the group as a whole. |
| Guest | Provide temporary access to users without regular accounts. | Restricts privileges to only allow the execution of basic tasks, limits access to system resources, and typically expires or gets deleted after a specific period or session. |
| Service | Created for applications, services, or daemons running on the server. | Permits apps to execute specific processes or services, often without interactive login capabilities, and limits access to system resources. |
| System | Created during the installation of specific software or services. | Allows specific apps to manage and execute system processes dedicated to specific system-related tasks. |
Now that we’ve explored all the different user roles we can have on our server, let’s see how to assign them:
1. Connect to your server either physically or remotely using SSH. Make sure you’re logging in from the root user account or using the sudo command to ensure that you have administrative privileges. This is a must to create users on your server.
ssh username@server_ip_addressReplace username with your username and server_ip_address with the IP address or hostname of your server, which should be provided to you by your hosting provider.
If you’re using a different port than the default port (22), you can specify the port number using the -p flag.
sudo ssh -p port_number username@server_ip_addressReplace port_number with the actual port number you use for your server.
2. Choose a suitable username for the new user, following naming conventions like lowercase letters, numbers, and underscores. Run the following command if you want to create a regular user:
sudo adduser usernameIf you want to create a new user and assign it a guest user, you can use this command:
sudo useradd -e YYYY-MM-DD usernameReplace username with the actual username that you want to create, and change YYYY-MM-DD to the date you want the user account to expire. The date must be specified using the YYYY-MM-DD format.
If you want to create a new user and assign it to a specific user group, use the following command:
sudo usermod -a -G groupname usernameReplace username with the actual username that you want to create, and replace groupname with the name of the group that you want to assign the new user to.
The -a flag ensures that the user is added to the group without removing them from any other groups they may already be a part of.
For example, to grant the new user sudo privileges, add them to the sudo group (Ubuntu) or the wheel group (CentOS):
sudo usermod -a -G sudo username # Ubuntu
sudo usermod -a -G wheel username # CentOS3. If your system doesn’t prompt you to enter a password, you can use the following command:
sudo passwd usernameMake sure to choose a secure password for the user account and include a combination of uppercase and lowercase letters, numbers, and special characters. When you’re entering the password, the characters won’t be visible as you type them.
After that, you will be asked to provide some additional information about the user, such as their full name, phone number, etc. You can either provide this information or press Enter to skip these fields.
Step 4: Manage Permissions
Another great way to up the security of your VPS is to manage and change the ownership of your files or directories to ensure that only the required access is provided. Essentially, permissions determine who has access to read, write, and execute files and directories on your server.
Here is the command you’ll need to change the ownership of a specific file or directory to a username and group:
sudo chown username:groupname /path/to/file_or_directoryThe chown command stands for “change owner”. Replace username, groupname, and /path/to/file_or_directory with the actual values.
If you want to change the permissions of a file or directory, you have to use this command:
sudo chmod permissions /path/to/file_or_directoryReplace permissions with the actual permissions you want to assign. These are the three different permissions:
| Permission | Symbol | Number Value | Function |
|---|---|---|---|
| Read | r | 4 | Allows you to only view the contents of a file or directory without being able to edit anything. |
| Write | w | 2 | Allows you to add, delete, or edit the contents of a file or directory. |
| Execute | x | 1 | Allows you to execute a file or enter a directory by running scripts. |
For instance, if you want to assign Read, Write, and Execute permissions for the Owner user, Read and Execute permissions to Group users, and only Read permissions for Guest (Other) users, your command will look like this:
sudo chmod 754 /path/to/file_or_directoryAlternatively, you could run it as such:
sudo chmod rwxr-xr-- /path/to/file_or_directoryThis is how we came up with the number 754 or rwxr-xr–, the – replacing the 0 values.
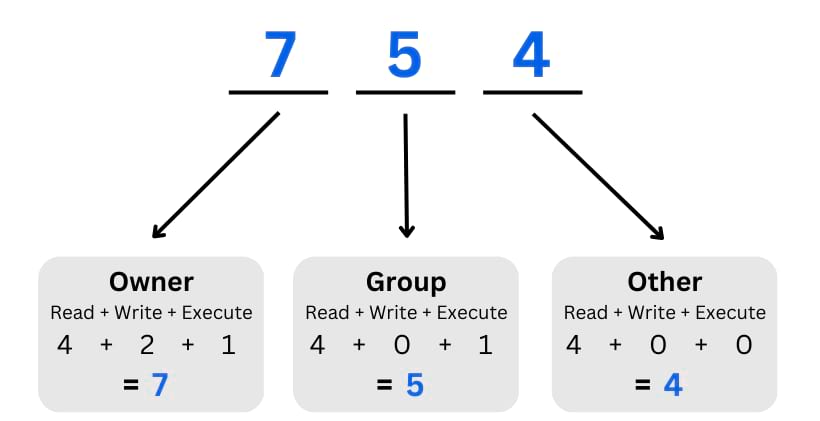
You should adhere to the Principle of Least Privilege (PoLP), which is rooted in the concept of minimizing risk. It advocates for a minimalist approach when it comes to granting privileges to users or software components on a server.
Rather than providing unrestricted access, this principle emphasizes the importance of granting the minimum set of privileges required for an individual or process to carry out their designated functions effectively.
This will help significantly enhance your server security and mitigate the potential risks that stem from granting excessive privileges, such as accidental or intentional misuse, system compromise, or the exploitation of vulnerabilities.
Step 5: Set Up a Firewall for Enhanced Security
A firewall is essentially a network security measure that monitors and controls incoming and outgoing traffic based on predetermined security rules. It acts as a barrier and the first line of defense, examining data packets and determining whether to allow or block their transmission.
Here is how you can set up a firewall on your server using two different methods: UFW and FirewallD.
Using UFW for Ubuntu (Debian-based) Systems
Uncomplicated Firewall (UFW) is a user-friendly command-line tool that simplifies firewall management on Linux systems. It provides an uncomplicated interface to create and manage firewall rules effortlessly.
To install UFW, enter the following command:
sudo apt update
sudo apt install ufwBy default, UFW denies all incoming connections and allows all outgoing connections. You can check the current settings by running this command:
sudo ufw status verboseIf you find that your permissions are set to the default, and you want to do that, run the following commands:
sudo ufw default deny incoming
sudo ufw default allow outgoingSince SSH is typically the primary means of accessing a remote Linux server, it is crucial to enable SSH connections explicitly:
sudo ufw allow ssh #Allow SSH connections (default port 22)Consider the services your VPS requires, such as web hosting or database management, then allow access to these services through specific ports using this command:
sudo ufw allow <port>/<protocol>Replace <port> with the relevant port number and <protocol> with either tcp or udp, depending on the service requirements.
For example:
sudo ufw allow 80/tcp #Allow HTTP traffic (port 80)
sudo ufw allow 443/tcp #Allow HTTPS traffic (port 443)
sudo ufw allow 123/udp #Allow NTP traffic (port 123, UDP)Once you have defined the necessary rules, enable UFW by typing:
sudo ufw enableYour new firewall permissions will automatically be enabled once you reboot your server.
Using FirewallD for CentOS (RHEL-based) Systems
Firewall Daemon (FirewallD) is a dynamic firewall management tool designed specifically for Linux operating systems. It provides a user-friendly interface to manage network traffic and offers a convenient way to configure and administer firewall rules.
Install FirewallD using the following command:
sudo yum install firewalldFirewallD operates with the concept of zones, which define the level of trust assigned to a network connection. By default, FirewallD provides a set of predefined zones, such as public, trusted, home, work, and internal. Each zone has a specific set of rules that govern the traffic flow.
Before making any modifications, verify the default zone assigned to your VPS. The default zone dictates the rules applied to network connections that do not match any specific zone.
sudo firewall-cmd --get-default-zoneIf the default zone is not set to your desired level of security, you can change it using the following command:
firewall-cmd --set-default-zone=<zone>Replace <zone> with the name of the desired zone, such as public, trusted, or internal. In some cases, you may need to modify the rules within a specific zone to suit your requirements.
As a rule of thumb, set the default zone to block all incoming traffic and allow all outgoing traffic using this command:
sudo firewall-cmd --set-default-zone=dropFirewallD offers an array of options for managing zones, including adding or removing services, ports, and IP addresses. For example, to set up basic rules to allow incoming SSH connections and deny all other incoming traffic, use the following command:
sudo firewall-cmd --zone=public --add-service=ssh --permanent
sudo firewall-cmd --reloadYou can do the same for other specific incoming traffic:
#Allow HTTP traffic (port 80)sudo firewall-cmd --zone=drop --add-port=80/tcp --permanentsudo firewall-cmd --reload
#Allow HTTPS traffic (port 443)
sudo firewall-cmd --zone=drop --add-port=443/tcp --permanentsudo firewall-cmd --reload
#Allow NTP traffic (port 123, UDP)
sudo firewall-cmd --zone=drop --add-port=123/udp --permanentsudo firewall-cmd --reload Once you have configured your zones and rules, activate FirewallD to enable it on your VPS by running the following:
sudo systemctl enable --now firewalldSetting up a firewall is not a one-and-done task. Make sure to always consider your specific needs carefully to be able to configure your firewall effectively and efficiently. Regularly reviewing and updating firewall rules is essential to maintain a secure environment.
Alongside this, monitoring firewall logs provides invaluable insights into firewall activities and helps identify potential security breaches. By default, firewall logs are stored in the system log files.
For Ubuntu systems, you can find them in the /var/log/ufw.log file, while CentOS systems store them in the /* file.
The importance of monitoring these logs cannot be overstated. Each connection attempt is recorded in the log files, allowing you to identify any suspicious activity, such as Distributed Denial-of-Service (DDoS) attacks, SQL injections, or malicious code.
For instance, a high volume of connection attempts from a single IP address may indicate a brute-force attack or an attempt to exploit system vulnerabilities. By promptly investigating such activities, you can take appropriate measures to mitigate the risks and fortify your defenses.
Managed vs Self-Managed VPS Hosting
When choosing a VPS hosting solution, you’ll need to decide between managed and self-managed options. With managed VPS hosting, such as Liquid Web’s managed VPS hosting, the provider takes care of server maintenance, security updates, and other administrative tasks. This can be an excellent option for those who lack the technical expertise or time to manage their VPS.
On the other hand, self-managed VPS hosting gives you full control over your server, allowing you to configure it to your exact needs. However, this option requires more technical knowledge and can be time-consuming.
Ultimately, the choice between managed and self-managed VPS hosting will depend on your specific needs and resources.
Best Practices and Optimization Tips for VPS Management
Effectively managing your VPS is crucial for maintaining security, performance, and reliability. Here are some best practices and tips for optimizing VPS management.
- Regular backups – Schedule regular backups of your VPS to ensure data recovery in case of hardware failure, data corruption, or security breaches. Store your backups offsite or with a reliable cloud storage provider for added protection.
- Monitoring server performance – Actively monitor your server’s performance, including CPU usage, memory usage, disk space, and network traffic. This will help you identify potential issues and optimize your server for better performance.
- Maintaining strong password policies – Implement strong password policies for all user accounts on your VPS, including using complex and unique passwords, changing passwords regularly, and avoiding the use of default or easily guessable passwords.
- Implementing multi-factor authentication (MFA) – Enable MFA for accessing your VPS to add an extra layer of security, making it more difficult for unauthorized users to gain access to your server.
- Keeping software up-to-date – Regularly update your server’s operating system, applications, and installed packages to ensure security and stability. Apply security patches promptly to address vulnerabilities and protect your VPS from potential threats.
- Configuring a firewall – Set up a robust firewall to protect your VPS from external threats and unauthorized access. Regularly review and update your firewall rules to maintain security.
- Staying informed about emerging security threats and vulnerabilities – Stay up-to-date with the latest security news, threats, and vulnerabilities that may affect your VPS. Regularly update your security measures to address these risks and protect your server.
- Implementing the principle of least privilege – Grant users the minimum permissions necessary to perform their tasks, reducing the risk of unauthorized access or actions. Regularly review user accounts and permissions to ensure they are appropriate and secure.
- Encrypting sensitive data – Use encryption to protect sensitive data stored on your VPS, such as customer information, passwords, and API keys. This will help prevent unauthorized access to your data in case of a security breach.
- Auditing and logging – Implement auditing and logging mechanisms to track user activities, server events, and security incidents. Regularly review your logs to identify potential issues and maintain security.
Choose Liquid Web for a Secure and Reliable VPS Hosting Solution
When it comes to selecting a VPS hosting provider, security and reliability should be top priorities. Liquid Web stands out as an ideal choice for businesses and individuals seeking a secure hosting environment, offering a range of features and benefits that set the company apart from the competition, including:
- Fully managed hosting – Liquid Web’s fully managed hosting takes the hassle out of managing your hosting infrastructure by providing proactive management, network security, and availability. This is especially beneficial for small and medium-sized businesses, as well as developers and IT professionals who may not have the time or resources to manage their hosting environment.
- High availability and 99.999% uptime – Reliable hosting ensures that your website or application is always up and running, minimizing downtime and providing a seamless experience for your users. This is crucial for eCommerce businesses, media and content providers, and enterprise-level businesses that depend on consistent performance.
- Customizable infrastructure – Liquid Web offers tailored solutions to fit the unique needs of your project, including designing custom, multi-server platforms, which helps enterprise-level businesses and those with complex hosting requirements to achieve their goals faster.
- Compliant solutions – Liquid Web’s secure and compliant hosting environment satisfies HIPAA or PCI requirements, ensuring that sensitive information will be protected. This is particularly important for eCommerce businesses and healthcare providers who handle sensitive data.
- Helpful human support – Liquid Web offers exceptional customer support, available 24/7/365, which ensures that you always have a knowledgeable team at your disposal, ready to help with any issues or questions that may arise.
- Transparent pricing and complimentary migrations – Liquid Web provides no-contract, transparent pricing, making it easy for new customers to switch to their hosting services. They also provide complimentary migrations for most hosting control panels, ensuring a smooth transition for your site, store, or application.
- Superb customer reviews – A plethora of reviews highlight customers’ satisfaction and the credibility of Liquid Web’s hosting services.
Liquid Web has provided exceptional service and support for our growing eCommerce business. Their fully managed VPS hosting has allowed us to focus on our core operations while knowing that our website is in good hands.“
– John D., eCommerce business owner
Secure Your VPS for a Safe and Stable Hosting Experience
By following best practices and optimization tips, you can effectively manage your VPS and protect it from potential threats and vulnerabilities.
That’s why Liquid Web offers a secure and reliable VPS hosting solution, making it an ideal choice for businesses and individuals seeking a secure hosting environment.
Don’t compromise on security and reliability when choosing a VPS hosting provider.