It’s all too common: Hackers target enterprises and cause data breaches that expose valuable data like payment information, software vulnerabilities, and business secrets.
Data breaches are increasing in frequency and can have a massive impact on your enterprise. With this in mind, keep reading to discover the state of data breaches in 2023 and how you can react in 2024.
This guide will teach you how to prevent data breaches by understanding the main threats and the corresponding security best practices.
In full, this data breach prevention guide includes:
Key points
- A data breach (or data leak) is a cybersecurity incident involving unauthorized access to sensitive data.
- Yahoo, Meta, and Microsoft have been the targets of three of the most recent and significant data breaches.
- Types of data breaches include malware, phishing, and brute force attacks.
- Enterprises experience financial losses, reputational damage, and legal consequences as a result of data breaches.
- Some of the most common reasons enterprises experience data breaches are insider attacks, using weak passwords, external bad actors, and failing to update apps and software.
- Preventing data breaches requires due diligence and proactive efforts like educating staff to prevent human error, implementing robust security measures, and choosing a web host that values security like Liquid Web.
Understanding data breaches
A data breach (or data leak) is a cybersecurity incident involving unauthorized access to sensitive data. The compromised data is often confidential information, personal details, intellectual property, or financial information like credit card numbers.
During or after the data breach, sensitive data may be viewed, changed, stolen, or transferred for illegal purposes.
A data breach usually refers to a digital attack, but physical resources, such as computer hard drives and paper records, can be subject to data breaches.
Data breach examples
Famous data breaches have shaken the public’s trust in large enterprises. Consider three recent examples.

Yahoo
With three billion accounts impacted, Yahoo experienced one of the most significant data breaches in history. Hackers capitalized on security flaws to steal customers’ personal information, including names, phone numbers, and passwords.
While the initial breaches occurred in 2013 and 2014, they weren’t publicly announced until 2016. Moreover, the true extent of the data breaches only came to light a year later.
Following the breach, Yahoo’s sale price to Verizon was reduced by $350 million, and the company had to pay hefty damages to some affected users.
Meta
The company behind Facebook is no stranger to information security incidents. In fact, 553 million accounts had personal data leaked in 2021, which resulted in a €265 million fine imposed by Ireland’s Data Protection Commission.
In 2023, the same commission fined Meta $1.3 billion for improper data transfers between the European Union and the U.S.
Microsoft
In May 2023, threat actors used fake authentication tokens to gain access to the emails of 25 organizations stored in the public cloud, including U.S. government agencies. They accessed 38 TB of private data in total during this security incident.
The examples above and similar public cloud attacks have encouraged large enterprises to switch to private cloud hosting with reputable web hosts like Liquid Web.
Types of data breaches
Cyberattacks are becoming increasingly sophisticated, but threat actors still use common approaches. Here are a few to be aware of to prevent enterprise data breaches.
Malware
The term “malware” is a portmanteau of “malicious” and “software.” Hackers aim to infect a computer with a software program with a hostile goal. One example is software that records the victim’s keystrokes — usually so their passwords can be isolated.
Ransomware is a notable type of malware that aims to render data or software inaccessible until the victim sends the hacker money. Ransomware attacks often target governments and large enterprises because of their ability to pay large sums and the persuasive threat of disrupting a service affecting millions of people.
Phishing
Cybercriminals can mimic legitimate communication from trusted sources like banks, delivery services, and insurance companies. This social engineering attack tricks people into providing sensitive information or exposing their devices to malware.
Emails are a common medium for phishing attacks, but phone calls and text messages are also used. Real-world events can also lead to phishing. For example, identity theft can happen when personally identifiable information (PII) is obtained from a brief look at someone’s ID card.
Enterprise staff should be alert to phishing attacks via email and social media platforms like LinkedIn.
Brute force
Hackers sometimes guess passwords using software that attempts every possible combination. In a brute force attack, millions of login credential possibilities are entered until the process of elimination reveals the right answer.
The growing threat of data breaches
According to the chief operating officer of Talion, a managed IT security service, the rise in data breaches can be attributed to poor investment in security and the increasingly advanced approaches used by cybercriminals.
With this in mind, large organizations must increase their time and investment in threat detection to prevent the consequences of data loss.
Effects of enterprise data breaches
The effects of a cyberattack are often wide-ranging and multifaceted. A single enterprise data breach can cause financial losses, reputational damage, and legal consequences.
Financial losses
According to IBM’s Cost of a Data Breach Report 2023, each data breach costs the affected company an average of $4.45 million. This average has increased by 15% in the past three years.
Downtime after a security breach drains enterprise finances. Unity Communications estimates that downtime costs $5,600 to $9,000 per minute, depending on the size of the enterprise.
This is due to lost revenue, responses to security issues, and patching up exposed weaknesses. As the adage goes, prevention is better than a cure, and this certainly holds true for enterprise data breaches.
Reputational damage
Data breaches can decimate consumer trust in your business, especially if you handle sensitive personal data, such as social security numbers.
Staff at some large enterprises have attempted to hide security issues to prevent reputational damage, but full transparency and swift action are needed when customer trust is at stake.
Legal consequences
If you fail to protect customer data or notify them about a breach, you could be fined by a government agency.
- U.S. state laws: All 50 American states have data breach notification laws. Moreover, 19 states changed or considered changing these notification laws in 2022. It takes diligence to stay up to date with data privacy.
- EU laws: If you operate in the European Union, you must follow the General Data Protection Regulation (GDPR). Consequently, if your company fails to comply, it could be fined up to €20 million or 4% of its yearly global revenue—whichever is higher.
- Healthcare-specific laws: If your company handles protected healthcare information in the U.S., you must adhere to the Health Insurance Portability and Accountability Act (HIPAA). Liquid Web offers HIPAA-compliant hosting to help you avoid hefty fines.
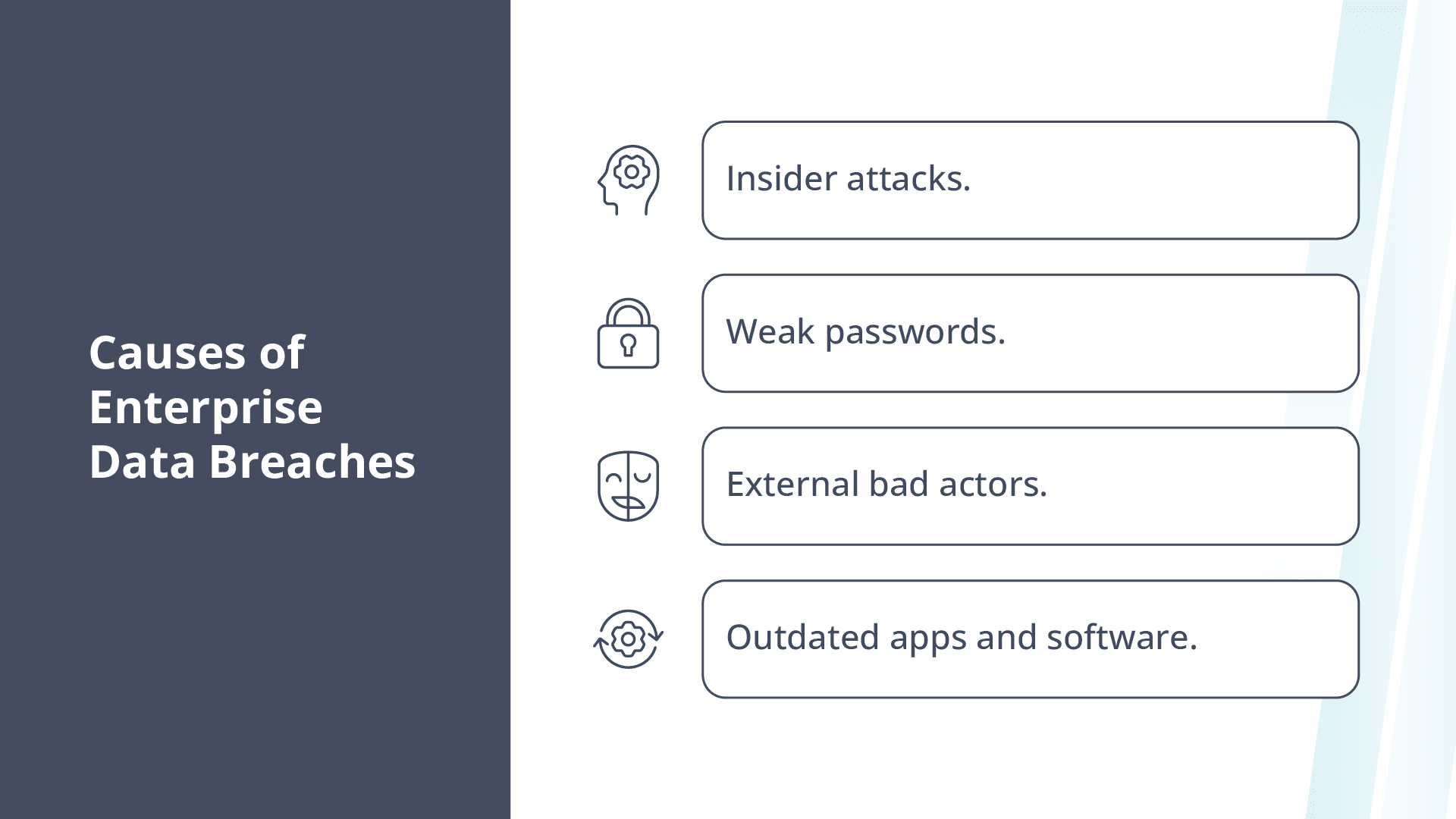
What causes enterprise data breaches?
The true origins of specific data breach incidents can be difficult to determine. That said, the common factors of enterprise data breaches are well-known, including:
- Insider attacks.
- Weak passwords.
- External bad actors.
- Outdated apps and software.
Insider attacks
As your enterprise grows and takes on more staff, the risk of an insider attack increases.
Weak passwords
NordPass, which offers a password management app, created a list of common passwords used by large enterprises in 20 industries and 31 countries. To many people’s dismay, NordPass found the most common passwords were “password” and “123456.”
External bad actors
Threat actors outside your company can conduct cyberattacks, often driven by financial gain. These individuals have many tricks up their sleeves and attempt to bypass your security defenses via malware, brute force, and social engineering attacks.
Outdated apps and software
Install updates as soon as they’re available on all business devices. These updates often contain security patches for identified vulnerabilities. If you have remote employees on personal or company devices, periodically remind them to update their software and apps.
Before making changes to your IT setup and operational policies, take some time to consider your enterprise’s unique circumstances and security goals. Use the following section to start.
Questions that avert an enterprise data breach
Instead of waiting for an enterprise data breach and then asking what went wrong, pose some preemptive questions to sniff out weak links in your company’s IT security setup. These are the illuminating questions you need to ask regarding data breach prevention.
Who
- Who has access to sensitive data? Minimize your total risk by ensuring each employee has only the security permissions they need.
- Who could stand to benefit from a security breach? An unscrupulous competitor, a resentful ex-employee, or an opportunistic cybercriminal could mount an attack.
- Who is best placed to help your enterprise protect data? Whether you rely on an internal or external IT team, have them generously staffed, equipped, and trained.
What
- What sensitive data does the company hold? This can be intellectual property, bank account details, social security numbers, or something else.
- What training does your staff have? New and seasoned employees alike must be taught to spot data breach vulnerabilities.
- What are competitors doing to prevent breaches? Gain context by examining rivals for your company’s size, industry, customer base, location, and resources.
Where
- Where is the sensitive data stored? Does your enterprise store critical info in the cloud, in servers on the premises, or somewhere else?
- Where are the main security vulnerabilities? For example, will you focus on strengthening your networks, tightening your endpoints, or switching to secure software solutions?
When
- When do security scans and updates take place? Scans should be frequent to prevent data breaches.
- When are you able to get help with an attack? Check the availability limits of the support teams you rely on. As the top hosting option, Liquid Web has 59-second average response time and 24/7/365 customer support, including on holidays.
How
- How often are passwords changed? Change passwords at least once every three months. If you suspect a password presents a risk, change it immediately.
- How much could an enterprise data breach cost you? Get a professional estimate based on your location, revenue, business size, and IT infrastructure.
Data breach prevention
- Educate staff to prevent human error.
- Identify security risks and mitigate them.Implement proper access control internally.
- Take stock of all data your company stores.
- Encrypt data.
- Strengthen passwords.
- Apply multi-factor authentication.
- Increase investment in security.
- Update software when prompted.
- Isolate your company’s resources.
- Use high-level security tools.
- Review your data security regularly.
- Choose a web host that values security.
Once you’ve gained context about your business in particular, consider how you’ll implement this checklist of best practices for enterprise data breach protection.
Educate staff to prevent human error
Bring in an external team to inform your staff on data protection habits and common security threats. After the initial training, schedule follow-up sessions to ensure staff are staying diligent.
Identify security risks and mitigate them
If employees are working remotely, systematically ensure their devices have proper security measures. Also, assess the security habits of your vendors and clients, starting with the main ones.
Implement proper access control internally
The more users can access data, the more vulnerabilities you have. Restrict data access to only those who need it and revoke their permissions once the job is complete. Additionally, save sensitive responsibilities for long-serving staff with good security knowledge.
Take stock of all data your company stores
A data stocktake aims to create an inventory or map that provides easily accessible details of all the data your company holds.
This level of data visibility facilitates regulatory compliance and helps you identify hidden vulnerabilities in various data sources.
Encrypt data
Use public key (asymmetric) or private key (symmetric) encryption. For example, SSL certificates let you transfer encrypted data over the web. If you choose fully managed web hosting from Liquid Web, you’ll get a free SSL certificate from Let’s Encrypt.
Strengthen passwords
Mandate passwords of a minimum length that use a number, uppercase letter, and special character. Moreover, enforce password changes at regular intervals.
Apply multi-factor authentication
This security approach requires two or more verification methods to access sensitive data. As part of a zero-trust security framework, it adds an extra layer of security to a complex password.
To illustrate, even if an outside attacker manages to crack your email password by brute force, MFA won’t let them in until they input a code that’s only accessible on your personal cellphone.
Increase investment in security
When it comes to security spending, you’re better safe than sorry. Ideally, install a robust firewall for your servers, acquire high-level antivirus protection, and task an external security team with performing an audit on your company.
Emerging technologies present an opportunity for you to invest in security and make savings in the long run. For example, according to IBM’s Cost of a Data Breach Report 2023, companies that invest in AI and automation for security save $1.76 million on average.
Update software when prompted
When software companies release updates, they often fix security vulnerabilities that put your company’s data at risk. Promptly install major software updates and ensure your staff members do, too.
Isolate your company’s resources
Shared hosting is a great low-cost option for growing businesses, but enterprises sustain more risk and should isolate their resources through virtualization or dedicated server hosting.
By isolating your data from server neighbors, virtually or physically, you add a layer of data protection to your IT setup.
Use high-level security tools
Whether you use a web application firewall (WAF) or a malware scanner, prioritize solutions catered to enterprises. An advanced solution that meets the needs of large enterprises is the F5 AIP intrusion detection system.
Review your data security regularly
Scan for viruses often and keep up to date on new cybersecurity trends. Schedule security audits by an internal or external security team.
Choose a web host that values security
Liquid Web offers DDoS protection and Server Secure Plus, featuring malware scanning and cleanup, anti-virus protection, and monthly vulnerability scans.
Final thoughts: How to prevent data breaches in 2024
By following the best practices above, you drastically decrease your risk of an enterprise data breach.
At Liquid Web, we take data breaches and other security threats seriously. All our web hosting clients enjoy robust security as standard, and our data centers are monitored 24/7.